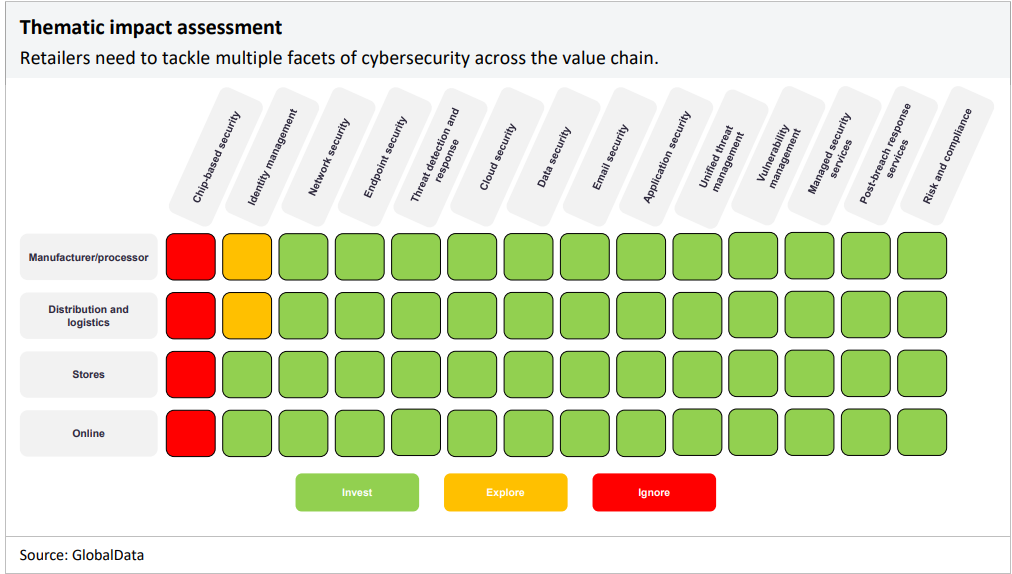
The matrix below details the areas in cybersecurity where retailers should be focusing their time and resources. We suggest that retailers invest in technologies that are shaded in green, explore the prospect of investing in technologies shaded in yellow, and ignore areas shaded in red.
Source: GlobalData Thematic Intelligence
Retailers need to adopt a holistic approach to cybersecurity to protect their large networks of data. Semiconductor (or chip manufacturing) is a capital-intensive area covered by trusted cybersecurity vendors rather than by retailers directly. Retail companies use a myriad of devices such as sensors, cameras, and other connected devices for warehouses, logistics, in-store consumer experience, and other business operations. Point-of-sale (POS) systems, ecommerce apps, and devices that carry customer and payment data are particularly vulnerable to cyberattacks. Hardware devices like smartphones and laptops are used to access the corporate network and can be a gateway for hackers to access a company’s sensitive data. Investment in cybersecurity across the value chain offers retailers the best chance of avoiding data breaches.
Here are the four main ways retailers should tackle cyberthreats:
- Adopt application security solutions that cover all their applications, from those used internally to popular external apps provided for use on customers’ mobile phones. IoT devices employed in the manufacturing process are linked to applications, and on the other side of the business, many consumers now pay for services and goods using mobile apps. Application security testing (AST)—the process of making applications more resistant to security threats by identifying security weaknesses and vulnerabilities—should be considered across the retail value chain.
- Train employees in identifying phishing emails and ensure that hackers cannot download malware onto these devices to access the network. Retail employees accessing internal IT and OT systems should also use more robust identification methods such as biometrics, which add an extra layer of cyber protection to regularly changing passwords.
- Use firewall as a service. This is a cloud-based service that allows companies to simplify their IT infrastructure and provides capabilities like web filtering, advanced threat protection (ATP), intrusion prevention system (IPS), and domain name system (DNS) security. The network across the retail value chain needs to be visible and its traffic constantly monitored, and access to the network must be stringently managed with zero trust network access (ZTNA).
- Undergo cyber security ‘fire drills’ to simulate worse-case scenarios in data breaches and pinpoint areas of vulnerability. Most retailers will likely incur a data breach, and post-breach response services must be in place to respond swiftly to any future attacks to reduce the potential damage. Vulnerability management, and risk and compliance services are needed to provide internal and third-party perspectives on points of cybersecurity weakness and areas for improvement.
How the challenge of ESG accelerates the need for cybersecurity According to GlobalData’s ESG
Framework, cybersecurity risk management falls under governance responsibilities for businesses. A retailer must ensure that their business is well protected against cyber threats and can safeguard the privacy of their consumers’ data. An important component of this is protecting personal consumer data like their address, financial information, and other PII.
Cyberattacks are a component of ‘hacktivism’ whereby hackers disrupt a retailer’s online platform rendering it unusable. Motivations for targeting retailers range from protesting a company’s product (i.e., vegan hackers would target a company specialising in animal products) to specific corporate policies. These attacks are less sophisticated than ransomware attacks and aim primarily for disruption. These attacks often involve defacing a company’s website, akin to graffitiing the entrance of a store, as well as spamming a company’s website via bots to overload the system and shut down their online operations—also known as Distributed Denial of Service (DDoS).
Hacktivism has been on the rise in recent years. In March 2022, hacker group Anonymous decided to target companies that were not pulling out of Russia fast enough in the outbreak of the Ukraine-Russo conflict. The hackers targeted retailers such as Auchan, Decathlon, and Leroy Merlin with DDoS attacks after the retailers were slow in halting operations in Russia.
Challenge | What’s happening? |
Productivity | Miners must ensure that they are increasing productivity by adopting the latest technology. Mechanization and monitoring are supporting improvements in productivity and lowering cost per unit output. |
Cost control | There is increasing upward pressure on costs to mining firms. Several factors have spurred this, including declining commodity prices, longer hail distances, falling ore grades, and rising material and labor costs. |
Supply chain | More disparate ore deposits are pushing mining into remote locations and developing nations. This gives rise to greater challenges in operating an efficient supply chain. |
Safety and sustainability | Given the worldwide shift to sustainability in the last few years, mining has come under increasing scrutiny for its damaging environmental practices. In addition, safety has become a concern. Mining firms must take more responsibility for ensuring that workers are properly protected on-site by taking active steps to avoid accidents and actively monitoring safety. |
Resource development | There is pressure on mining firms to continuously identify viable new mines. This is made more difficult by an environment of declining ore grades. Furthermore, there are rising development costs and more remote deposits. |
COVID-19 | COVID-19 has posed a massive threat to the mining industry. The main fear is that there could be an outbreak at a mine, which would force operations to a halt, impacting both costs and productivity greatly. This has led to operational challenges, including continuous testing of staff and reducing capacity at mines to enforce social distancing. |
Source: GlobalData Thematic Intelligence
How the challenge of digitalisation accelerates the need for cybersecurity
All aspects of retail are being digitalised—from the initial manufacturing of products in the warehouses to the customer who pays for the product with a contactless credit card in stores, via mobile apps, or online. In store, the process of purchasing products has gone almost completely digital. According to the European Payments Landscape in 2030 report, published in 2021, 89% of respondents said that they either frequently or sometimes use contactless cards. 57% had used mobile wallets such as Apple or Samsung Pay. PoS devices involved in financial transactions need to be protected, as they are the most vulnerable. Hackers are primarily interested in financial data and personal details they can sell.
Endpoint security can help reduce risks associated with contactless payment systems. Emerging biometric payment systems (like using fingerprints or facial recognition systems to pay) promise to be safer. Credit card details can be obtained easily – using someone’s unique facial or hand features would prove more difficult for hackers.
How the challenge of future of work accelerates the need for cybersecurity
Collaboration tools and cloud systems allow retail employees to work more flexibly from home. However, these tools also present a vulnerability for retailers. Those working from home need to be able to work on secure networks. It is now more common for hackers to download malware into employee laptops through phishing emails, which gives them access to the company network and sensitive data. Corporate IT is less able to assist someone working from home or control their actions, devices, and software.
It is important, therefore, to ensure that employees are taught cybersecurity housekeeping skills so they can identify cybersecurity risks, such as phishing emails. Software needs to be updated regularly with antivirus protections to reduce cyber risks that come with working from home.
How the challenge of geopolitics accelerates the need for cybersecurity
A year after the Colonial Pipeline ransomware attack in the US, which took place in May 2021, cyber-risks to critical national infrastructure and businesses remain. Cybersecurity attacks are a new tool in the arsenal of nation states who want to undermine the IT infrastructure of another. This has an impact on retailers who may be caught in the crossfire.
IoT devices are very vulnerable to cybersecurity risks employing robots, sensors in cameras, and other connected devices will have to do regular security checks on these devices. Networks protected by third-party tech providers are also not immune to cyberattacks. For example, the Kaseya ransomware attack led to the Swedish supermarket chain Coop closing 500 stores (cash registers no longer functioned due to what was dubbed an IT attack). This attack was orchestrated by REvil targeting managed service providers, in this case, Kaseya, and their customers in a massive supply chain attack. It is likely that in the future, cyberattacks will be used as a weapon, impacting high-profile retail chains.
How the challenge of the online shift accelerates the need for cybersecurity
According to GlobalData market forecasts, global online retail sales are expected to reach approximately $5tr worldwide by the end of 2026. Covid-19 accelerated the trend toward shopping online, with many people stuck in lockdown globally. This online shift means that retailers are carrying more sensitive consumer data than ever before. The need to carefully protect and manage this data cannot be understated. Many global retail companies have experienced a data breach in the last decade and forked out millions in settlements as a result. Home Depot paid out a least $134.5m to credit-card companies in 2014 following a huge data breach that exposed the financial information of over 50 million customers. This was one of the largest settlements paid out in retail history.
Security teams need to manage vast IT and OT systems to cope with more operations going online. It is not enough to perform manual checks. Security checks on IT and OT systems should also include automated, AI-powered systems. Hackers who manage to get hold of consumer data can deceive those same customers by creating phishing emails (e.g., fake online receipts) to lure them into downloading malware onto their devices and stealing personal and financial data. Employees must also receive training to manage online platforms and identify threats to the network.
GlobalData, the leading provider of industry intelligence, provided the underlying data, research, and analysis used to produce this article.
GlobalData’s Thematic Intelligence uses proprietary data, research, and analysis to provide a forward-looking perspective on the key themes that will shape the future of the world’s largest industries and the organisations within them.